Nist Cloud Security Guidelines
The nist definition of cloud computing author.
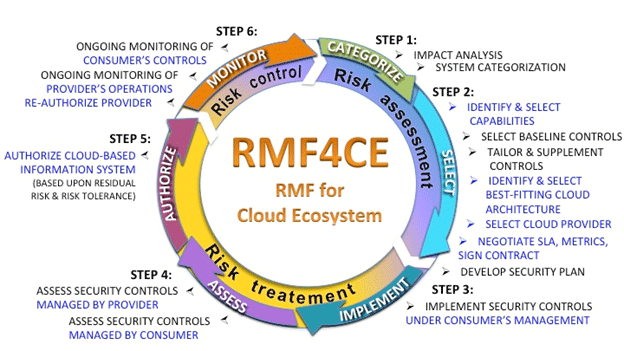
Nist cloud security guidelines. While aspects of these characteristics have been. Cloud security guidelines and recommendations found in public private sources such as. Appendix d of nist sp 800 171 provides a direct mapping of its cui security requirements to the relevant security controls in nist sp 800 53 for which the in scope cloud services have already been assessed and authorized under the fedramp program. The national institute of standards and technology nist has been designated by the federal chief information officer cio to accelerate the federal government s secure adoption of cloud computing by leading efforts to identify existing standards and guidelines.
Nist cloud computing public security working group white paper challenging security requirements for us government cloud computing adoption december 2012 c. Nist computer security division csd keywords. Cloud security guidelines and recommendations described in open source literature such as nist or fedramp that address known or theorized cloud security concerns or considerations that have the potential to impact cloud data security. Mills vm leakage and orphan control in open source clouds proceedings of ieee cloudcom 2011 nov.
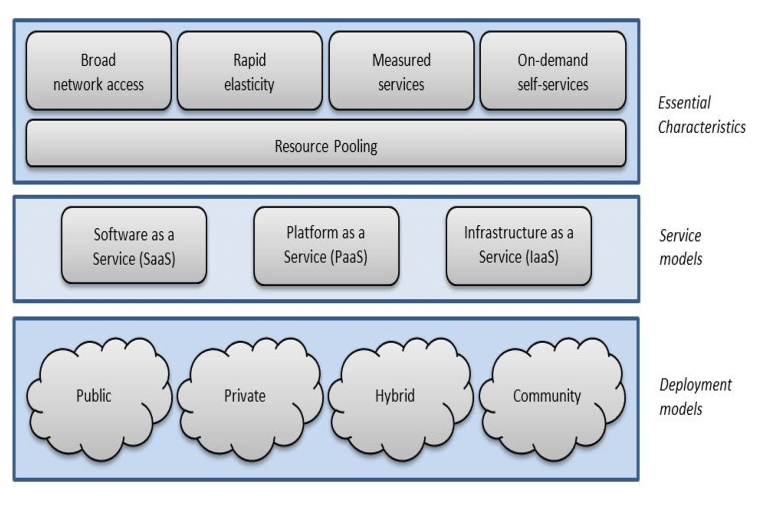
Abstract cloud computing can and does mean different things to different people. Cloud computing can and does mean different things to different people. Nist sp 800 145 the nist definition of cloud computing cloud computing saas paas iaas on demand self service reserve pooling rapid elasticity measured service software as a service platform as a service infrastructure as a service created date. The national institute of standards and technology nist has finalized its first set of guidelines for managing security and privacy issues in cloud computing.
Cloud computing has been defined by nist as a model for enabling convenient on demand network access to a shared pool of configurable computing resources e g networks servers storage applications and services that can be rapidly provisioned and released with minimal. The common characteristics most interpretations share are on demand scalability of highly available and reliable pooled computing resources secure access to metered services from nearly anywhere and displacement of data and services from inside to outside the organization.