Nist Cyber Security Framework Wiki

Cybersecurity framework executive order.
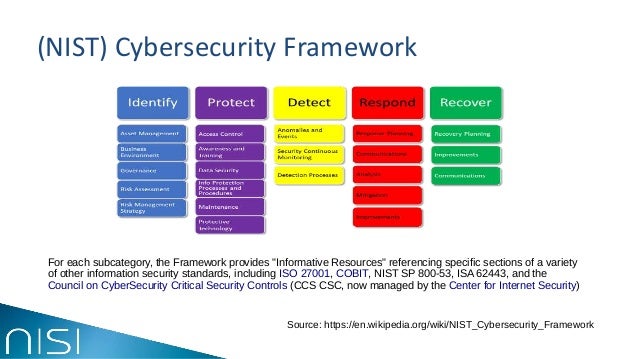
Nist cyber security framework wiki. The nist cybersecurity framework nist csf provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage those outcomes it is intended to help private sector organizations that provide critical infrastructure with guidance on how to protect it along with relevant protections for privacy and civil liberties. The publication serves as a fundamental reference to support a workforce capable of meeting an organization s cybersecurity needs by establishing a taxonomy and common. Overview nist cybersecurity framework provides a policy framework of computer security guidance for how private sector organizations can assess and improve their ability to prevent detect and respond to cybersecurity attacks nist cybersecurity framework provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage those outcomes. A database of nearly one thousand technical controls grouped into families and cross references.
Special publication 800 12 provides a broad. The nice cybersecurity workforce framework nice framework nist special publication 800 181 is a national focused resource that categorizes and describes cybersecurity work. Guidelines for smart grid cybersecurity nistir 7628 revision 1 introduction to nistir 7628. It is published by the national institute of standards and technology which is a non regulatory agency of the united states department of commerce nist develops and issues standards guidelines and other publications to assist.
Starting with revision 3 of 800 53 program management controls were identified. A maturity based framework divided into five functional areas and approximately 100 individual controls in its core nist sp 800 53. Nist special publication 800 53 provides a catalog of security and privacy controls for all u s. Introduction to the roadmap the roadmap is a companion document to the cybersecurity framework.
Nist smart grid framework status report. The framework has been translated to many languages and is used by the governments of japan and israel among others. Federal information systems except those related to national security. The nist cybersecurity framework provides a policy framework of computer security guidance for how private sector organizations in the united states can assess and improve their ability to prevent detect and respond to cyber attacks.
Japanese translation of the nist cybersecurity framework v1 1 page not in english this is a direct translation of version 1 1 of the cybersecurity framework produced by the japan information technology promotion agency ipa portuguese translation of the nist cybersecurity framework v1 1. On september 22 24 2020 the iapp will host a virtual workshop on the development of a workforce capable of managing privacy risk. The introduction to the framework roadmap learning module seeks to inform readers about what the roadmap is how it relates to the framework for improving critical infrastructure cybersecurity the framework and what the roadmap areas are. Check out nist s new cybersecurity measurements for information security page.